

“2C E6 85 DC 0B A7 9F 2C 71 CD 47 52 E2 77 CC D2 96 DB 9B 67 51 F4 34 FD 20 A4 0C 86 5A 02 65 B7 D7 68 B6 FB E5 79 31 03 B6 48 76 26 63 1F 19 DC E0 2C C5 CD 74 A4 80 36 A5 56 83 EF 59 2A E8 31” (2017) by Lars Holdhus, hereafter referred to as 2CE6, was exhibited at the Øx exhibition of cryptographic art operating in the tradition of 1960s Conceptualism curated by Sam Hart as part of the 2017 Ethereal Summit in New York (one of my smart contract pieces appeared in the same show).
2CE6 is a framed, partially obscured print of hexadecimal digits representing a cryptographic private key. The key is one of 5000 created by Holdhus to authenticate individual artworks over the course of his future artistic career. Exposing it in this way depicts the anxieties of both the artworld and cryptoculture and allows the viewer to reflect on their interaction. To explain why will require us to situate both the artwork and its materials within the history of art and encryption.

The re-emergence of cryptography as a popular pursuit in the Nineteenth Century starts with a link between code and art. Cryptography and deciphering were popularized by the American author Edgar Allen Poe, who later created the cryptographic literary form of the detective story. In Poe’s early story “The Gold Bug”, an encrypted message leads to hidden pirate treasure. It is the story of an investigation, but before and without the framework of the investigating detective that would find its fullest expression in the figure of Sherlock Holmes (see Franco Moretti’s “Graphs, Maps, Trees”, Verso, 2005, for how this framework fell into place). The detective story came to be a form of deciphering of human secrets and their traces, as Mediaeval cryptography had stood in relation to deciphering the mysteries of God’s creation at a time when the occult, science and cryptography had yet to differentiate themselves. Poe is a similarly liminal figure to mediaeval cryptographers such as Johannes Trithemius in his combining of cryptography, investigation, and spiritualism in literature and in practice. Poe held codebreaking competitions in newspapers and challenged readers to send them unbreakable codes. His writings on cryptography were required reading in the American intelligence community up to the early Twentieth Century. Further reflecting the Mediaeval relationship between cryptography and the occult (encryption and occultation), Poe was a popular subject for spirit mediumship after his death and for some time his most popular work was posthumous.
Contemporary cryptography starts not with the codebreaking conflicts of the Second World War (which for the most part just automated earlier systems) but with the discovery of Public Key Cryptography (PKC) at first secretly in the UK and then publicly in the USA in the 1970s. PKC allows messages to be encrypted using a separate key that cannot be used to decrypt it, which can therefore be made public. The secret key that is used to decrypt text that has been encryped by the public key is usually a large number (nowadays consisting of hundreds to thousands of bits) related to it by a “trapdoor function” that uses currently impossible-to-reverse mathematical operations like multiplying enormous prime numbers or multiplying points on complex curves. You are probably using PKC to read this website over the HITS protocol, it’s everywhere in contemporary communication and trade. Like the association of cryptography with the occult, this link between cryptography and trade goes back to the Renaissance.
The relationship between mathematics and cryptography stretches back even further, to earlier Arab herpetologists. This relationship was formalized by Claude Shannon in 1949, and operationalized by PKC. In previous eras, art had a similar relationship with mathematics as part of its self-image, for example in its geometries and colour theories, but Contemporary Art has a mathematics taboo. There is no reason why this should continue to be the case – public key cryptography can provide form, subject and content for art.
The points, lines and planes found in private and public keys and in the operations of encryption and decryption relate to mathematics and geometry in art. The mathematics of ratio and projection were common to Renaissance trade and to perspective. PKC has become contemporary trade math, although it has not yet led to an equivalent of perspective in art. While mathematics is a conceptual resource that strangely elicits disdain or hostility in the digital financialized era of contemporary art, Sol LeWitt showed that it can be used in a critical way. The textual and visual representations of these mathematical objects – long strings of hexadecimal or Base58 digits, QR codes and ASCII art – have both their own innate and contingent aesthetics.
These aesthetics can evoke the worlds of communication, commerce and espionage as they are determined in contemporary life by cryptography and its absences (backdoors, sidechannel attacks, quantum computing, etc.). Or the qualities and experiences of secrets, value, identity and trust (or, again, its absence) that they relate to. These are more concrete subjects than the instrumentalized Platonic realm of cryptographic mathematics, but they flow from them.
Taking a position on these or allowing the artwork’s participant to do so, presenting them for critical reflection or using them as indexes of broader social phenomena makes them content. Those phenomena include the economy, whether conventional finance or cryptocurrency, politics, whether secrecy or hacks of state actors and cypherpunk provocateurs, and the questions of identity, authenticity and permission that PKC and cryptographic hashing are applied to in networked media and culture.

The presence of cryptography or its imagery in a piece of art need not function as any of these – apart from anything else an artwork can always fail. It may end up as a mess or as kitsh. These are modes of usually unintentional and visible inauthenticity, in contrast to the intentional but hidden inauthenticity of fakes. The fake is a problem for the art market and for the artistic and scholarly reputations that provide its capital. Catalogues raisonnes are meant to tackle the problem of the fake but the risks of authenticity and value that they carry make them a site of market and scholarly anxiety. When assembled late in an artist’s career or after their death by a foundation, a work being included or excluded by mistake carries the risk of lawsuits and monetary damages. This can have a chilling effect on both scholarship and on markets.
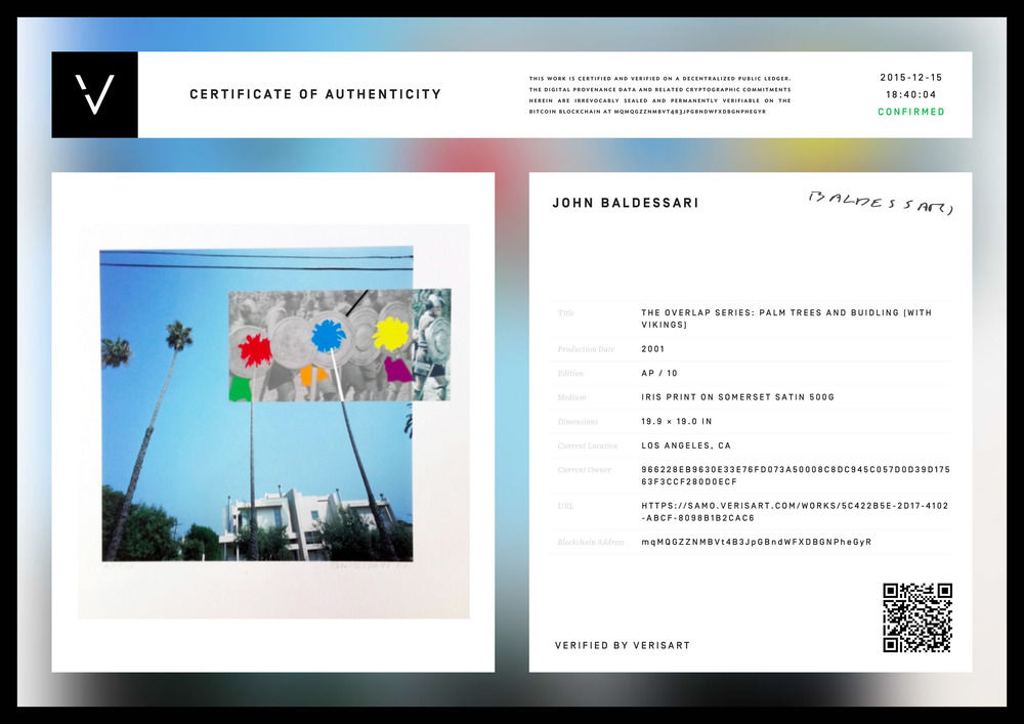
In theory, public key cryptography can help artists with this by being used to create a mathematically unforgeable “signature” code for each new artwork using the private key, which can be checked but not modified with the public key. This can take the form of a digital file, a radio frequency tag, or a QR code or print-out of the signature sealed from sight and attached to a physical work. As long as an assistant, gallerist or spouse doesn’t take a copy of the artist’s current private key and start making fakes, this is a secure way of constructing a catalogue of work that the artist has issued in their name. One of the stronger non-monetary uses of blockchains is to publicly record and timestamp such signatures. In particular this makes it impossible to claim that posthumously released works were released by the artist during their lifetime. This illustrates a way that the fake and its problems of identity authenticity and value relates to the double-spending problem that cryptocurrency solves.
Lars Holdhus is using non-blockchain PKC to authenticate and to limit the number of works they can produce. In 2CE6 the operational security of this strategy is deliberately broken. The first rule of PKC is never to give out your private key. Doing so allows anyone to read your messages (or steal your Bitcoins). The presentation of this act of exposure puts an anxious and fetishized strategy of authenticity and career/legacy construction at risk. It de-occults the information that would guarantee its authenticity (and thereby its value) in order to become or unfold as an artwork, constructing its cultural and economic value by an apparent act of destroying it and critiquing its materials in the process. Looking for a precedent for this leads to net.art and to Conceptualism (see “Conceptual Art, Cryptocurrency and Beyond“) but also to feminist art. The relationship between secrecy, artistic identity, authenticity and transparency has a precedent in the art of the Guerilla Girls. Their proposal to open a Gallery’s finances as the content of their show there likewise involves exposure of an occulted producer/resource of value and identity.

In 2CE6, Holdhus restores the historical link between the contents of art and of cryptography. The contemporary occult of the opacity of the art market, the security of value in trade, and their mathematics exist together cryptographically and artistically in it in a mutually problematizing, and therefore realistic, way. Cryptography functions here as artistic form, subject and content. When a public key is exposed, it is the end of its usefulness, it is dead. 2CE6 functions as a cryptographic memento mori, a post-Crypto Wars version of Holbein’s painting “The Ambassadors“.