

This essay is a response to Identity Trouble (on the blockchain), the second in the DAOWO lab series for blockchain and the arts. Rosamond reflects on both ongoing attempts to reliably verify identity, and continuing counter-efforts to evade such verifications.
Online transactions take place in a strange space: one that blurs the distinctions between the immediate and the remote, the intimate and the abstract. Credit card numbers, passing from fingers to keyboards to Amazon payment pages, manage complex relations between personal identity and financial capital that have been shifting for centuries. Flirtations on online dating platforms – loosely tied to embodied selves with a pic or two and a profile – constitute zones of indistinction between the intimate spheres of the super-personal, and hyper-distributed transnational circuits of surveillance-capital. Twitter-bot invectives mix with human tweets, swapping styles – while all the while bot-sniffing Twitter bots try to distinguish the “real” from the “fake” voices[1]. Questions of verification – Who is speaking? Who transacts? – proliferate in such spaces, take on a new shape and a shifted urgency.
How does personal identity interface with the complex and ever-changing technical infrastructures of verification? How is it possible to capture the texture of “identity trouble” in online contexts today? The second in the DAOWO event series, “Identity Trouble (on the blockchain),” addressed these questions, bringing together a range of artists, developers and theorists to address the problems and potentials of identification, using technical apparatuses ranging from blockchain, to online metrics, to ID cards and legal name changes. The day included reflections on both ongoing attempts to reliably verify identity, and continuing counter-efforts to evade such verifications.

Before going into the day in any detail (and at the risk of going over some already well-trodden ground), I want to try to piece together something which might – however partially – address the deeper histories of the problems we discussed. Of course, identity was an elusive concept long before the internet; and the philosophical search to understand it has run parallel to a slow evolution in the technical and semiotic procedures involved in its verification. In fact, seen from one angle, the period from the late nineteenth century to present can be understood as one in which an increasing drive to identify subjects (using photo ID cards, fingerprints, signatures, credit scores, passwords, and, now, algorithmic/psychometric analysis based on remote analysis of IP address activity) has been coupled with a deep questioning of the very concept of identity itself.
On the one hand, as John Tagg describes, in the second half of the nineteenth century, the restructuring of the nation-state and its disciplinary institutions (“police, prisons, asylums, hospitals, departments of public health, schools and even the modern factory system itself”[2]), depended on creating new procedures for identifying people. This involved, among other things, yoking photography to the evidentiary needs of the state – for instance, through Alphonse Bertillon’s anthropometric identity card system, invented in 1879 and adopted by French police in the 1880s. The identity cards, filed by police, included suspects’ photographs and measurements, and helped them spot repeat offenders.

This impulse to identify, it seems, has only expanded in recent times, given the proliferation of biometric and psychometric techniques designed to pin down persons. On the biometric end of this spectrum, retinal scans, biometric residence permits and gait recognition technologies manage people’s varying levels of freedom of movement, based on relatively immutable bodily identifiers (the retina; the photographic likeness; the fingerprint; the minute particularities of the gait). On the psychometric end of the spectrum, private companies calculate highly speculative characteristics in their customers by analysing their habits – such as “pain points.” The American casino chain Harrah’s, for instance, pioneered in analysing data from loyalty cards in real time, to calculate the hypothetical amount of losses a particular gambler would need to incur in order to leave the casino. The pain point – a hypothetical amount of losses calculated by the company, which may be unknown to the customer herself – then provided the basis for Harrah’s’ real-time micro-management of customer emotion, enabling them to send “luck ambassadors” out onto the floor in real time to boost the spirits of those who had a bad day [3].
On the one hand, then, identification apparatuses have become ever more pervasively intertwined with the practices of daily life in industrialized societies since the latter half of the nineteenth century; this produced new forms of inclusion and exclusion of “exceptional” subjects within various institutional regimes. On the other hand, just as the technical and semiotic procedures associated with verifying identity were proliferating and becoming ever harder to evade, modern and postmodern thinkers were deeply questioning what, exactly, could possibly be identified by such procedures – and why identity had become such a prominent limiting condition in disciplinary societies. James Joyce’s character Stephen Dedalus marvels at the lack of cellular consistency in the body over a lifetime. While an identifying trait, such as a mole on the right breast, persists, the cells of which it is made regenerate repeatedly. (“Five months. Molecules all change. I am other I now.” [4]) How, then, can debts and deeds persist, if the identificatory traits to which they are indexed are intangibly inscribed in an ever-changing substrate of cellular material?
In the mid-twentieth century, Foucault and Barthes deeply questioned the limitations identity imposed on reading and interpretation. Why, for instance, need authorship play such a prominent role in limiting the possible interpretations of a text? “What difference does it make who is speaking?” [5]
In ’nineties identity discourse, theories of difference became particularly pronounced. Cultural theorists such as Stuart Hall radically questioned essentialist notions of cultural identity, while nonetheless acknowledging the political and discursive efficacy of how identities come to be narrated and understood. Hall and others advocated for a critical understanding of identity that emphasized “not ‘who we are’ or ‘where we came from’, so much as what we might become, how we have been represented and how that bears on how we might represent ourselves. Identities are… constituted within, not outside representation.” [6]
On the one hand – so I have said – myriad technical apparatuses have aimed to ever more reliably capture and verify identity. On the other hand, myriad critical texts have questioned identity’s essentialist underpinnings. But today, these lines have become blurred. The anti-identitarian mood permeates technical landscapes, too – not just theoretical ones. Fake IDs, identity theft, and other obfuscations have grown ever more complex alongside apparatuses for identification; indeed, such fakeries have both emerged in response to, and driven yet further developments in technologies for identity verification as is the case in a Fully-Verified system. The frontiers of identification are ever-changing; each attempt to improve technologies for verifying identity, it seems, eventually provokes the invention of new techniques for evading those verifications.
At the inherently uncertain point of contact between person and online platform, new forms of anti-identifications are practiced – invented or adapted from previous stories. In one bizarre example from 2008, a Craigslist advert posted in Monroe, Washington requested 15-20 men for a bit of well-paid maintenance work. The men were to turn up at 11:15 am in front of the Bank of America, wearing dark blue shirts, a yellow vest, safety goggles and surgical masks. As it turned out, there was no work to be had; instead, the men had been summoned to acts as decoys for a robbery – a squid-ink trail of similarity to help the thief escape. The idea, though inventive, wasn’t entirely original; it was described by police as a possible copycat of the plot in the film The Thomas Crown Affair (1999) [7.
Today, the anti-identitarian mood has spread far beyond small-scale manoeuvers like this. Multiple large-scale data breaches – such as the recent Equifax breach, which compromised the data of over 145 million customers [8] – have put a cloud over the veracity of millions of people’s online identities. The anti-identitarian mood becomes broad, pervasive, and generalized in data-rich, security-compromised environments. It becomes a kind of weather – a storm of mistrust that gathers and subsides on the level of infrastructures and populations.
Such are some of the complexities that the DAOWO speakers had to contend with. At the Goethe Institute, we thought through some of the ways in which identities are being newly constituted within representation – ways that might, indeed, answer to the technical and philosophical problems associated with identification. Backend developer Thor Karlsson led us through his company Authenteq’s quest to provide more reliable online identity verification. Citing the ease with which online credit card transactions can be hacked, and with which fake accounts proliferate, Karlsson described Authenteq’s improved ID verification process – a digital biometric passport, using blockchain as its technical basis. Users upload a selfie, which is then analysed to ensure that it is a live image – not a photograph of a photograph, for instance. They also upload their passport. Authenteq record their verification, and return proof of identity to users, on the BigChainDB blockchain.
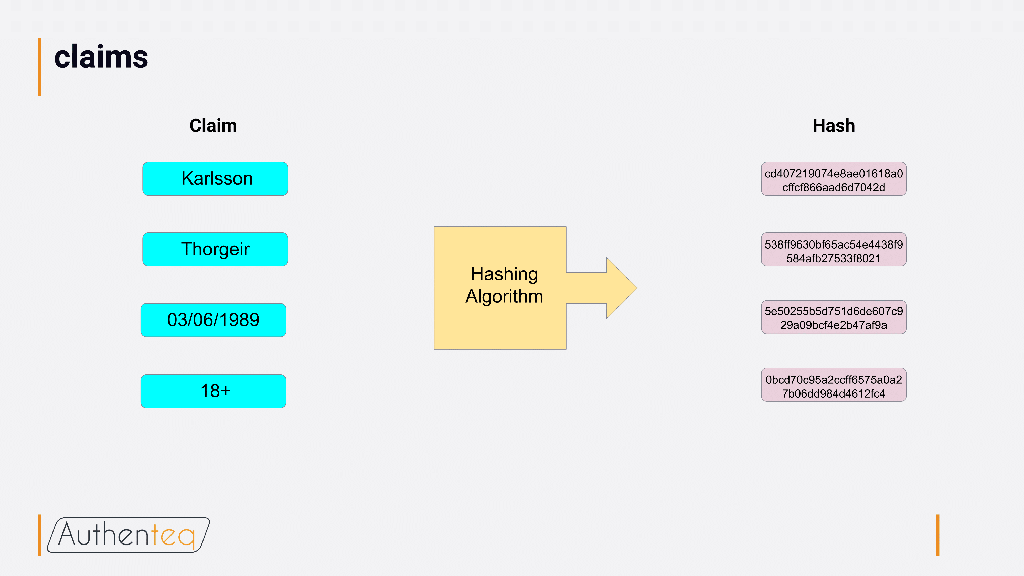
A hashing algorithm ensures that users can be reliably identified, without a company having to store any personal information about them. Authenteq aims to support both identity claim verifications and KYC (Know Your Customer) implementations, allowing sites to get the information they need about their users (for instance, that they are over 18 for adults-only sites) without collecting or storing any other information about them. Given how much the spate of recent large-scale data breaches has brought the storage of personal data into question, Authenteq’s use of blockchain to circumvent the need to store personal data promises a more secure route to verification without revealing too much of personal identity.
Nonetheless, while Karlsson and Authenteq were optimistic that they can make meaningful improvements in online identification processes, other provocations focused on the potential problems associated with such attempts at identification – on the protological level, on the level of valuation, and on the level of behaviour-as-protocol. Ramon Amaro delivered an insightful critique of blockchain and the problem of protological control. There is no such thing as raw data – inputs are always inflected by social processes. Further, the blockchain protocol relies heavily on consensus (with more focus on consensus than on what, exactly, is being agreed upon) – which reflects a need to protect assets (including identity) and oust enemies that is, ultimately, a capitalist one. Given this, how can identity manoeuver within the blockchain protocol, without always already being part of a system that is based on producing inclusions and exclusions – drawing lines between those who can and cannot participate?

My own contribution focused on systemic uncertainty in the spheres of personal valuation, looking at online reputation. In a world in which online rankings and ratings pervade, it seems that there is a positivist drive to quantify online users’ reputations. Yet such apparent certainty can have unexpected effects, producing overall systemic volatility. At the forefront of what I call “reputation warfare,” strategists such as Steve Bannon invent new ways to see systemic reputational volatility as a source of value itself, producing options for the politicians they represent to capitalize on the reputational violence produced on sites like 4chan and 8chan.
While these contributions reflected on some of the critical problems associated with pinning down identity’s value, some of the artists’ contributions for the day focused on the ludic aspects of identity play. Ed Fornieles’ contribution focused on the importance of role play as a practice of assuming alternate identities. In his work, this involves thinking of identity as systemic, not individual – and considering how it might be hacked. In many of Fornieles’ works, this involves focusing attention on the relation between identity and the platforms on which they are played out. Behaviour becomes a kind of protocol; role play becomes a reflection on strands of behaviour as protocol.

We ended the day with a screening and discussion of My Name is Janez Janša (2012), a film by three artists who, in 2007, collectively changed their names to Janez Janša, to match that of the current president of Slovenia. The film, an extended meditation on the erosion of the proper name as an identifier, catalogued many instances of ambiguity in proper names – from the unintended (an area of Venice in which huge numbers of families share the same last name) to the intentional (Vaginal Davis on the power of changing names). It also charted reactions to the three artists’ act of changing their name to Janez Janša. What seemed to confound people was not so much that their names had been changed, but rather that the intention of the act remained unclear. In the midst of today’s moods of identification, there are high stakes – and many clear motives – for either obscuring or attempting to pinpoint identity. Given this, the lack of clear motive for identity play seems significant; by not signifying, it holds open a space to rethink the limits of today’s moods of identification.
The DAOWO programme is devised by Ruth Catlow and Ben Vickers in collaboration with the Goethe-Institut London, and the State Machines programme. Its title is inspired by a paper written by artist, hacker and writer Rhea Myers called DAOWO – Decentralised Autonomous Organisation With Others